Accelerate application security testing with Burp Suite. Each new version of Burp Suite shares a common ancestor.
FEATURES
Burpsuite Professional
Intercept everything your browser sees
A powerful proxy/history lets you modify all HTTP(S) communications passing through your browser.
Break HTTPS effectively
Proxy even secure HTTPS traffic. Installing your unique CA certificate removes associated browser security warnings.
Manage recon data
All target data is aggregated and stored in a target site map – with filtering and annotation functions.
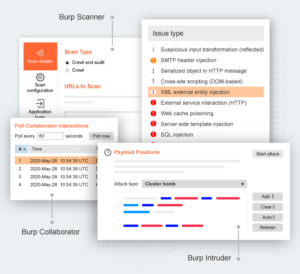
Manually test for out-of-band vulnerabilities
Make use of a dedicated client to incorporate Burp Suite’s out-of-band (OAST) capabilities during manual testing.
Expose hidden attack surface
Find hidden target functionality with an advanced automatic discovery function for “invisible” content.
Speed up granular workflows
Modify and reissue individual HTTP and WebSocket messages, and analyze the response – within a single window.
Work with WebSockets
WebSockets messages get their own specific history – allowing you to view and modify them.
Quickly assess your target
Determine the size of your target application. Auto-enumeration of static and dynamic URLs, and URL parameters.
Faster brute-forcing and fuzzing
Deploy custom sequences of HTTP requests containing multiple payload sets. Radically reduce time spent on many tasks.
Scan as you browse
The option to passively scan every request you make, or to perform active scans on specific URLs.
Automatically modify HTTP messages
Settings to automatically modify responses. Match and replace rules for both responses and requests.
Burpsuite Enterprise
Easy scan set-up
Point and click scanning – just a URL required. Or trigger via CI/CD.
Out-of-box configurations
Perform a variety of scans, such as a fast crawl or a critical vulnerability audit, with ease.
Burp Scanner
Catch the latest vulnerabilities with Burp Scanner. Frequently updated, research-fuelled scanning engine. Trusted at over 13,000 organizations.
All major CI/CD platforms
Integrate with platforms including Jenkins and TeamCity. See vulnerabilities in your development environment.
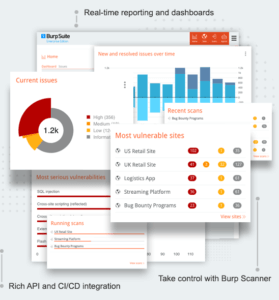
Vulnerability management platforms
Integrate scanning and security reporting into your own management and orchestration systems.
Role based access control
Multi-user, role-based functionality for site hierarchy, scan detail and reporting. Give everyone control.
Multiple deployment options
Deploy on-premise, or to cloud. Managed Kubernetes clusters on AWS (beta) and Azure (beta).
Rich email reporting
Get reports emailed to the right members of your team, to tailor your communications effectively.
Aggregated issue reporting
Organize issues by their class at the touch of a button. Focus on the vulnerabilities you want to fix.
Scan as you browse
The option to passively scan every request you make, or to perform active scans on specific URLs.
Automatically modify HTTP messages
Settings to automatically modify responses. Match and replace rules for both responses and requests.
Reach out to learn about the Plans & Pricing
Email : vijay@aditech.in